Adding tests for CVEs to Linux Smart Enumeration is something that I've been wanting to do for a while. However I wanted to do it better than what I've seen in the past with many existing CVE suggesters and testers. Many of these had a lot of false positives so when you get the results they are many times useless and you just have to manually testing them.
The main objective of Linux Smart Enumeration is to provide as concise information as possible. Only showing more in depth or less relevant information when the user requests it. I want it to keep it that way also for the CVE tests.
However the script must also be distributable as a single file so it is easy to use (copy from server to server, fast download to use process, etc) and also has to be easy to maintain so I can extended as needed either by me or by contributors.
With all that in mind, I decided to add a new section called cve inside the main script, where I am reusing the whole test process to run specific tests for the different CVEs that I want to include. These CVE tests are being added to a cve directory in the Linux Smart Enumeration repository where also a skel.sh file is placed so it can be used as a template. Now, to include the CVE tests in the main script, the are first packaged with a new tool called package_cvs_into_lse.sh (quite self explanatory).
This way, when you run:
$ tools/package_cvs_into_lse.shThis will generate a new script called lse_cve.sh which contains the CVE tests inside.
These tests are compressed with gzip and encoded in base64. During execution, they are uncompressed, decoded and evaluated so each one of them can be processed as a single test.
Due to the requirement of this build process and to still provide a single script file that can be just downloaded and used. Now each versions is published in the GitHub releases page, where you can download the lse.sh script with all the CVE tests already included.
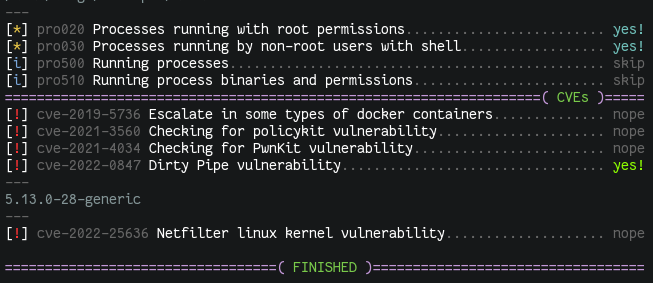
Note that the one-liners in the README file are already updated to use the releases URL.
At the time of writing this, only a few CVE tests have been included, which will hopefully also serve as examples for contributors.
If you want to contribute with more CVE tests, please, read the comments in the skel.sh file and check the existing cve test files.